Share single service via WireGuard
from syaochan@feddit.it to selfhosted@lemmy.world on 15 Sep 2025 21:29
https://feddit.it/post/21750924
from syaochan@feddit.it to selfhosted@lemmy.world on 15 Sep 2025 21:29
https://feddit.it/post/21750924
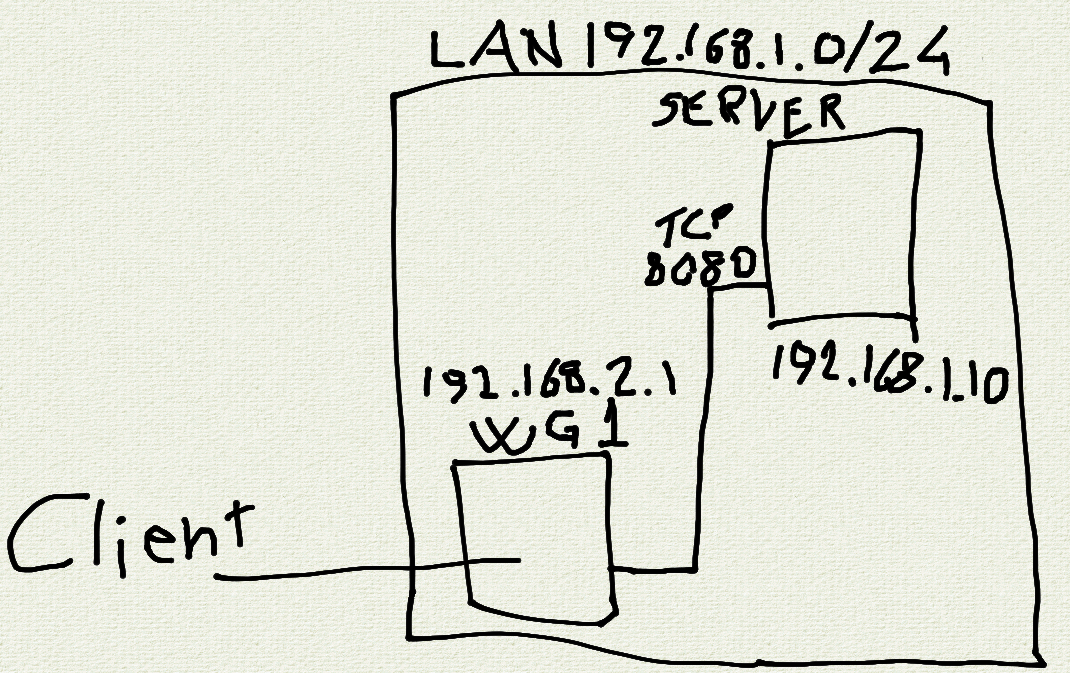
I wanted to share a service I’m hosting, but didn’t feel comfortable just leaving publicly accessible, even behind a reverse proxy. In the meantime I did not want to give access to my whole lan with a VPN, or redirect all internet traffic from a client thru my network. So the idea is to run a WireGuard instance on my OpenWRT router in a completely isolated zone (input, output and forward set to reject on firewall) and then forward a single port from the service host’s. Client is android, so using WG Tunnel and split tunnel just for the relevant app should not impair client’s network access. Initial tests seems to be ok, is there anything I may have overlooked? Please feel free to comment.
#selfhosted
threaded - newest
Seems fine with me. I have been playing around with some MikroTik devices doing exactly this. It should also be possible to achieve the same using OpenWRT. You do indeed have to isolate things using different subnets and route certain IP-adresses between those IPv4 subnets. Nothing too complicated.
Let me make sure I understand everything correctly. You have an OpenWRT router which terminates a Wireguard tunnel, which your phone will connect to from somewhere on the Internet. When the Wireguard tunnel lands within the router in the new subnet 192.168.2 0/24, you have iptable rules that will:
So far, this seems alright. But where does the service run? Is it on your LAN subnet or the isolated 192.168.2.0/24 subnet? The diagram you included suggests that the service runs on an existing machine on your LAN, so that would imply that the router must also do address translation from the isolated subnet to your LAN subnet.
That’s doable, but ideally the service would be homed onto the isolated subnet. But perhaps I misunderstood part of the configuration.
The service runs on another machine with address 192.168.1.10, so a different subnet than the WireGuard one, hence the port forward. I confirmed that this works, I can reach the service from phone on mobile data connected to WireGuard endpoint.<img alt="" src="https://feddit.it/pictrs/image/bea88178-c033-4a75-a22e-49c068ba7944.png"> wg1 is in zone dmz <img alt="" src="https://feddit.it/pictrs/image/045ff80f-7c67-40a6-a781-5b13e2e71a97.png"> this is the port forward
OpenZiti allows to only allow predefined ports/services via VPN: netfoundry.io/docs/openziti
Thanks for the link, I did not know this service. I’m still a bit reluctant to use commercial solutions which may do a rug pull in the future.
Tailscale would probably be easier for this. Install tailscale on the server and configure only that service available in the tailscale dashboard. I’ve used this method for ssh access to family members devices.
I’m sure you could run the same setup using headscale (tailscale self hosted), it would require a bit more setup though and dynamic dns would probably have to be working.
I know about Tailscale, but since it’s a commercial service I’m not keen to adopt it and then maybe they stop having a free tier. I’ll look into Headscale instead, I did not know about that before.
Is there a way for a Wireguard peer to advertise AllowedIPs similar to Tailscale’s subnet routings? If that’s right, perhaps you can configure your host’s address as one of the AllowedIPs on the OpenWRT peer, and skip port forwarding too
Yes, since Tailscale is based on wireguard.
Probably not the best practice, though, since any device that connects will be allowed to use the service if there is no authentication on the cert.
I’m not sure if I understood, but on the host there are other services I do not want to share outside my LAN. My goal was to share a single service.
I think this is exactly what Pangolin was designed for and does.
Isn’t Pangolin just a reverse proxy?
The connection between your Pangolin service (hosted outside your network) and your LAN is through a VPN. Essentially you’re creating a proxy that you can point your domain address at which isn’t your house’s IP address. Plus then everything inside your network is still secure behind your VPN.
So you connect to Pangolin, and Pangolin routes the traffic to your network.
If I understood correctly I should either get a VPS to host Pangolin or use their cloud. This would increase the costs right?
Yes, correct. You can always locally host it as there are other benefits like unifying user credentials for all your hosted services. But its primary design is to be hosted externally.
currently I host everything locally, but I don’t like the fact that anyone visiting my domain can easily find my address.
I’m in the process of determining on if I set up Pangolin myself or not. Another huge benefit is higher availability. (ex. If my internet goes down at home, I won’t know until I try to connect, but if I have an external service and it’s monitoring that connection, it can inform me when it loses connection)
Price is certainly something to consider when weighing its value for your setup
With firewall you could do it pretty properly
You don’t really need forwarding as you don’t need NAT here.
A part of the filtering can be done by wireguard by setting the allowed IPs correctly. Just check if only one service is listening on the server port you’ll allow.
Now a question: all without tls right? ;)
Could you elaborate what you mean with setting the allowed IPs? Yes, without tls.
Apologies for the delay. On the VPN termination point, you have to set the allowed IP addresses. On the case of a client, a /32 is enough. It means that only this IP would be receiving responses. A client with a different IP address would be able to inly send packets, not to get any back, thus not able to get a TCP session. I think it is enough and rhat no additional FW rule is needed.
Don’t worry, there’s no deadline here. I’m not sure I got it so I’ll try to explain what I understood. You’re saying that I have to set a single IP address for the client, and allow that single address to connect to service on port 8080 on 192.168.10.1 in the firewall, right? I’m not too confident in my ability to configure the firewall, so I thought that completely isolate the subnet 192.168.2.0 and then forward a single port to it was the safe choice.
Why the downvote?
unrelated: ever heard of draw.io? excalidraw, even.
Now I have. Is this a roundabout way to say you did not appreciate my touchpad art? /j